Blog
Comparison of Digital and Quantum Computers, Part 2: Factorization
Everyone in the IT field is interested in how big a threat quantum computers are to cryptography and how to deal with the problem. This series of articles tries to explain this problem in a popular way. After the Introduction, we can look at the problem of factorization.
The RSA Algorithm and the Factorization Problem
Let's start with the factorization problem. The best way to attack this algorithm is provided by the so-called GNFS (General Number Field Sieve). This provides a list of pairs of numbers. If we multiply these numbers together, we should get the desired product. Then, we need to test the given pairs of numbers for primality. If we want to find out the approximate number of operations, we need to know the complexity of the GNFS algorithm itself, which can be calculated based on information about the length of n the factored number. We give this length in bits.
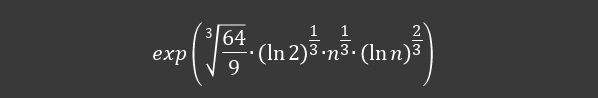
An important part is determining the number of number pairs. This data is usually in units
of pairs, the exception is the situation when the primality verification fails for some
reason during generation. This data therefore works as a kind of indicator. Based on further
tests, the aforementioned indicator can warn, for example, about an inappropriate choice
of testing algorithm. So, ideally, we will get one result, or five results. If there are
more than ten, there has probably been a failure somewhere and it is advisable to check the
entire mechanism.
In any of these cases, a test for primality of the expected pairs follows. Since the number
of tests is small, there is no significant change in complexity. However, the correct choice
of testing algorithms is important. Among the applicable ones are the following:
- AKS (Agrawal–Kayal–Saxena primality test, cyclotomic AKS test), which is used only for smaller bit ranges due to its high computational complexity. This test is impractical for numbers above 256b. The advantage is its deterministic output, the test has a complexity of approximately O(n6)
- Baillie-PSW is based on the Miller-Rabin test and the complementary Lukas test. It has no range restrictions, it is a heuristic test with a complexity of approximately O(n log n log[log n]).
- ECPP (Elliptic Curve Primality Proving/Elliptic Curve Primality testing) tests are based on the work of Shafi Goldwasser and are applicable up to the range of 105+1 bit. This is again a deterministic This is again a deterministic test with complexity of O(n4)
- Miller-Rabin is a probabilistic test, usable with keys up to about 4kb in size. The problem is the probabilistic output, to ensure adequate conclusiveness it is necessary to implement more than tens of tests. As a rule, 40-100 passes are used, the total complexity of the algorithm is O(kn log2n log[log n]) where k is the number of bases.
So we know how many logical operations are needed, but how to convert this into instructions
for a 64b CPU? Based on the requirements, it is necessary to solve the creation of the matrix
(120 instructions per step) and then the analysis of the matrix content (5 instructions per step).
Then the results must be tested for primality. This calculation applies to numbers that fit into
the processor registers. As soon as the prime numbers are larger, the calculation begins
to become more complicated. Of course, the number of operations for creating the matrix increases
in a similar way and slightly for analyzing it. From this, it is possible to approximately
determine the total number of instructions.
In a similar way, we can also find the total memory requirement. The amount of memory required
to create the GNFS matrix is approximately:
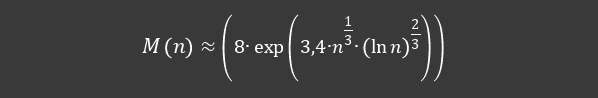
Based on the above approximate calculations, we have estimates that we can use to calculate the required machine time, the related power consumption and the amount of memory needed to complete the given task. The task will be to factorize the key in order to find out what is within the capabilities of individuals, organizations or our civilization, or what is completely beyond our capabilities. For our own calculation, we will consider a hypothetical computer with 10 cores at a frequency of 1GHz, without hyperthreading, the power consumption of this computer will be an ideal 100 W. Based on the previous information, the following results are obtained:
| n-bit | Complexity | Factorization | Instructions | Memory (B) | Time (years) | Energy (J) |
| 512 | 275.2 | 1.757∙1019 | 2.19∙1021 | 6.75∙1012 | 6.96∙105 | 2.19∙1015 |
| 1024 | 2101.6 | 1.316∙1026 | 1.64∙1028 | 2.58∙1017 | 5.21∙1012 | 1.64∙1022 |
| 2048 | 2136.4 | 1.533∙1035 | 1.91∙1037 | 2.86∙1023 | 6.07∙1021 | 1.91∙1031 |
| 2540 | 2149.3 | 3.527∙1038 | 4.40∙1040 | 4.99∙1025 | 1.39∙1025 | 4.40∙1035 |
| 3072 | 2161.7 | 5.805∙1041 | 7.25∙1043 | 6.95∙1027 | 2.30∙1028 | 7.25∙1037 |
| 4096 | 2182.2 | 1.289∙1047 | 1.61∙1049 | 2.55∙1031 | 5.11∙1033 | 1.61∙1043 |
| 7168 | 2229.3 | 2.539∙1059 | 3.17∙1061 | 4.01∙1039 | 1.00∙1046 | 3.17∙1055 |
| 8192 | 2242.1 | 5.708∙1062 | 7.13∙1064 | 6.88∙1041 | 2.26∙1049 | 7.13∙1058 |
| 13550 | 2296.9 | 1.178∙1077 | 1.47∙1079 | 2.40∙1051 | 4.66∙1063 | 1.47∙1073 |
| 37100 | 2444.2 | 3.952∙10115 | 4.94∙10117 | 1.16∙1077 | 1.56∙10102 | 4.94∙10111 |
| 76608 | 2591.4 | 1.342∙10154 | 1.67∙10156 | 5.64∙10102 | 5.32∙10140 | 1.67∙10150 |
Unfortunately, the reality will be extremely different. If there is not enough memory, access
to data during the calculation will be slowed down due to the need to access the data storage.
This is an expansion of the order of 103 for NVMe disks, 104 for SSD
disks and 107 for HDD - spinning disks. At the same time, memory in the order of
TB is needed for the 512b number itself. The memories themselves have a consumption that
corresponds to another approximately 100W per 1.5 TB. This corresponds to a small increase
in power consumption in decimal places. Furthermore, especially when analyzing a matrix that
is huge in size, the data does not fit in the processor cache. This leads to so-called
cache-misses, i.e. these are memory-intensive operations. However, any such access needs
to reload the memory contents into the cache, together with problems with branch prediction
in the code, this will mean a loss of approximately 200 cycles. No calculations will
be performed during this time. Overall, this can result in a slowdown of approximately
5 orders of magnitude (105 to 109 depending on the technologies used).
Are we capable of carrying out such an attack? We can look at it from several perspectives:
- AMD have produced an estimated billions of processors in their entire history (we can consider 50 years), so we are in the order of 109 . Since the first processors had a single core for several decades and only after 2006 did multiple cores begin to be used, it is possible to consider an average of 2.5 cores per processor. The considered available performance will reduce the time accordingly, but in the overall range this performance will rather eliminate the small fluctuation caused by problems with the availability of large data in the processor cache.
- If we consider only time, the universe was created 18 billion years ago. This corresponds to the order of 1010, so we are not able to perform such a calculation fast enough.
- If we consider only the required power input, we can think as follows. The entire human civilization had an electrical power input of around 30,000 TWh in 2025, i.e. in the order of 1016 Wh. The sun provides us with a source with a capacity of 1017 W (what we receive on the Earth's surface), so if we wanted to freeze, we could use the energy. In the case of harnessing the entire sun, we are talking about a source with a power of 1026 W. The central black hole of our galaxy is then capable of providing 1029 W and the entire galaxy approximately 1037 W. It is clear that even these sources are not sufficient.
To be continued in the section Algorithms Using the Discrete Logarithm Problem (February 23th 2026)
References:
- Sage Math script - RSA Factorization
Source: https://cryptosession.info/ke-stazeni - A Tale of Two Sieves
Source: https://www.ams.org/ - On Polynomila Selection for the General Number Field Sieve
Source: https://www.ams.org/




